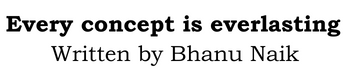This article describes how to disable SMBv1 client driver in Windows Server Operating System. Following settings applicable for Windows Server 2022, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2 Machines.
A server message block (SMB) protocol is a network protocol that allows applications on a computer to share files with other computers and to request services from server programs. . The SMB client can also send and receive requests through any server program that is configured to receive SMB requests.
File-sharing and printer sharing are supported by Windows via the SMB protocol directly hosted on Transmission Control Protocol (TCP).
Below are the version of Server Message Block (SMB) client and server components.
- SMB version 1 (SMBv1)
- SMB version 2 (SMBv2)
- SMB version 2.1
- SMB version 3 (SMBv3)
- SMB version 3.02
- SMB version 3.1.1
In order to operate as a client-server protocol, SMB requires a server (Lanman Server) and a client (Lanman Workstation).
1.0 of SMB contains a bug that can be exploited to take over remote computer control.
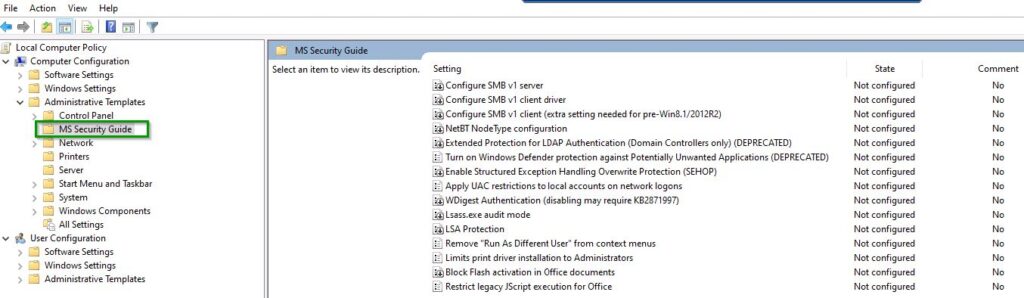
Configure SMB v1 client driver is set to Enabled: Disable driver
SOLUTION:
By default, the MS Security Guide Group Policy settings are not available in any windows server operating system.
Computer Configuration\Policies\Administrative Templates\MS Security Guide\Configure SMB v1 client driver
We need append below Administrative Template files (ADMX/ADML). It can be downloaded from windows Microsoft security website.
- SecGuide.admx
- SecGuide.adml
Extract the zip files from your download , you can find Windows Server-2019-Security-Baseline-FINAL\Template\SecGuide.admx now Copy SecGuide.admx file into your windows machine path → C:\Windows\PolicyDefinitions
Windows Server-2019-Security-Baseline-FINAL\Template\en-US\SecGuide.adml now copy SecGuide.adml file into your windows machine path → C:\Windows\PolicyDefinitions\en-US
As soon as above changes has been done, run gpedit.msc (or) gpmc.msc as administrator from the command prompt.
Now Edit the policy and Enabled: Disable driver (recommended) click on Apply and OK as shown below.
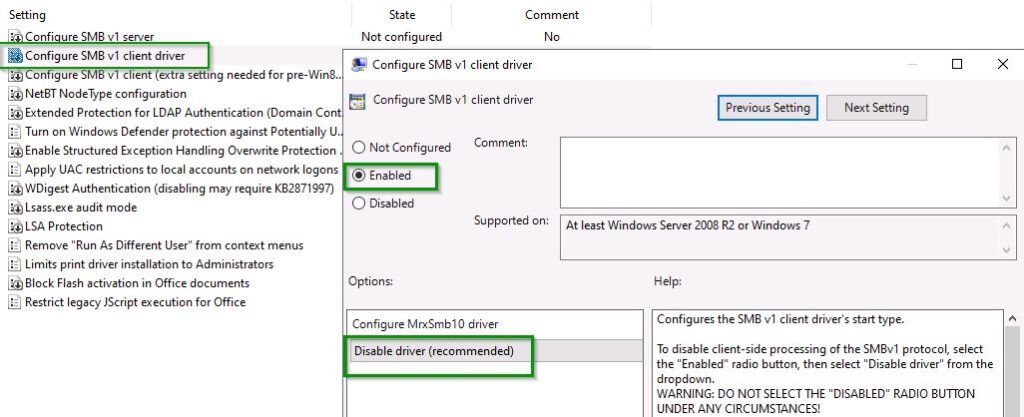
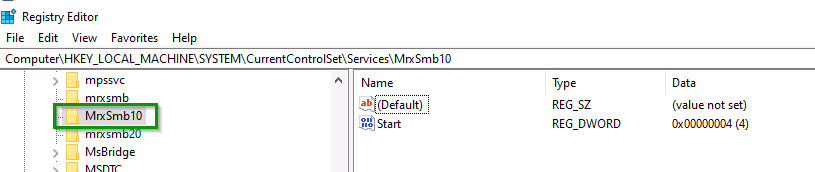
In addition, we can also double check that the changes to the group policy settings have been replicated in Windows Registry as shown below path.
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MrxSmb10
SMB v1 client driver MrxSmb10 is visible in Windows Registry
Reboot the machine once to apply these changes permanently.
Conclusion:
Disable SMBv1 client driver in Windows server Operating System. Protecting assets while strengthening their cybersecurity posture is achievable with the direct mitigations and supporting controls included in Exploited Protocol Server Message Block.
If you have any questions about topic, please leave a comment.