In this article discussed about SSH Prefix Truncation Vulnerability (Terrapin) in Microsoft Windows Operating System.
SSH Prefix Truncation Vulnerability (Terrapin) fixing procedure is same for Microsoft Windows Operating System and Linux Operating System (RHEL, CENTOS).
In below scenario OpenSSH Server configuration for Windows Server 2019.
SSH Prefix Terrapin attack:
By using the Terrapin attack, an attacker with access to the PAN-OS management network [ machine-in-the-middle attacks] can use less secure authentication algorithms when connecting to PAN-OS software and downgrade connection security.
A vulnerability discovered via the Terrapin Attacks has underscored the importance and ongoing relevance of advanced vulnerability management patching strategies and vulnerability prioritization, particularly in hybrid enterprise environments where even SSH is vulnerable. Associated CVEs: CVE-2023-48795
SSH Prefix Truncation THREAT:
Over 10 years ago, OpenSSH introduced newer cryptographic algorithms and encryption modes that exploit vulnerabilities in the SSH transport layer protocol, causing the Terrapin attack. Since then, these have been adopted by a wide range of SSH implementations, therefore affecting most current implementations.
IMPACT:
The impact in practice will depend largely on the supported extensions. An attacker who successfully exploits the vulnerability may be able to downgrade the security of an SSH connection when using SSH extension negotiation. RSA public keys are most commonly used for client authentication, so this will impact client authentication security.
Terrapin Vulnerability Truncation SOLUTION:
Terrapin requires an adversary-in-the-middle (MiTM) position at the network layer to intercept and modify handshakes, so either ChaCha20-Poly1305 or CBC with Encrypt-then-MAC must be used to secure the connection.
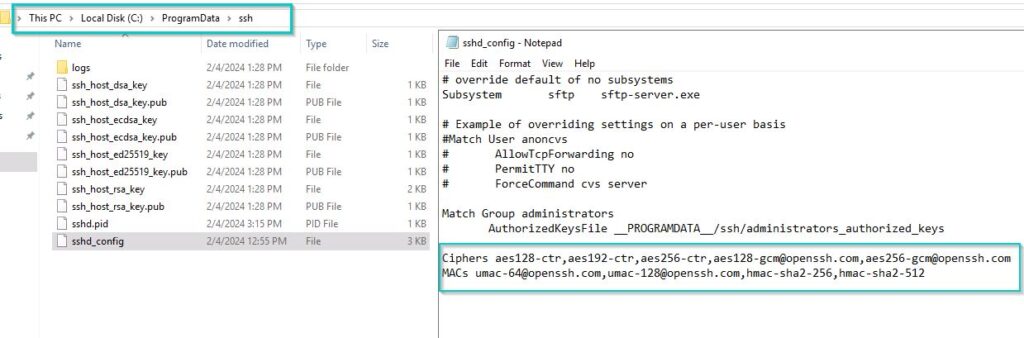
Login into Microsoft Windows Server Operating Systems and Local Disk (C:) and enable Hidden items. By default, C:\ProgramData is hidden folder.
In Local Disk (C:) you can find ProgramData and navigate to ssh folder as shown below C:\ProgramData\ssh
Edit the sshd_config in a notepad and add below Ciphers and MAC Algorithms.
Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com MACs umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512
After adding the Ciphers and MAC Algorithms save it and reboot the machine. Vulnerability fixed successfully.
conclusion:
SSH Prefix Truncation Vulnerability (Terrapin) solution has been explained. This procedure is same for Microsoft Windows Operating System and Any Linux Operating System.
Thanks for your time, leave a comment if you have any queries about SSH Prefix Truncation Vulnerability Windows.