In this article discuss about Disable diffie-hellman-group1-sha1 for SSH in Linux Operating System. In security scans like Tripwire, it is found to be a vulnerability in Centos/RHEL Machine as explained below.
A key exchange algorithm that uses diffie-hellman-group1-sha1 plays a vital role. Red Hat Enterprise Linux (RHEL) and Community ENTerprise Operating System (CentOS). Currently supports and enables the algorithm that security/vulnerability scanners like Tripwire may identify as vulnerable.
To achieve maximum security, inferior OpenSSH key exchange methods should be disabled.
On RHEL8/CENTOS8, this article covers how to disable the diffie-hellman-group1-sha1 key exchange mechanism.
In cryptography, signature hash functions which use asymmetric cryptography to distribute the public key to verify the hash information and maintain the confidentiality of the secret key used to create the hash are examples of mechanisms that are used to safeguard information integrity.
In cryptography, asymmetric cryptography can be used to protect the integrity of information, for example, signed hash functions, which enable the distribution of public keys for verification of hash information.
Vulnerability about diffie-hellman-group1-sha1 for SSH
Vulnerability
Vulnerability Name ⇒ SSH Key Exchange with SHA1 Hash Algorithm Enabled
Published ⇒ 2016-01-08
Strategy ⇒ Data-Driven Attack
nCircle ⇒ 476395
CVSS ⇒ v2:4.3
CVSS ⇒ v3: 5.9
DESCRIPTION
The SSH server has enabled support for a key exchange algorithm protected with the deprecated SHA1 hashing algorithm. Collisions occurring with deprecated hash algorithms can undermine connection security as demonstrated with the SLOTH attack research.
SOLUTION
Disable sha1 based key exchange algorithms:
– diffie-hellman-group1-sha1
– diffie-hellman-group14-sha1
– diffie-hellman-group-exchange-sha1
Affected Applications Application Name: SSH
Procedure to Disable diffie-hellman-group1-sha1 for SSH
Step1: Edit /etc/sysconfig/sshd and uncomment the following line.
#CRYPTO_POLICY= to CRYPTO_POLICY=
Whenever you do that change, you opt out of the server’s crypto policies. To enable or disable system-wide crypto policies, comment CRYPTO_POLICY= and run update-crypto-policies
Step2: Run the below command to check active key exchange algorithm
more /etc/crypto-policies/back-ends/openssh.config
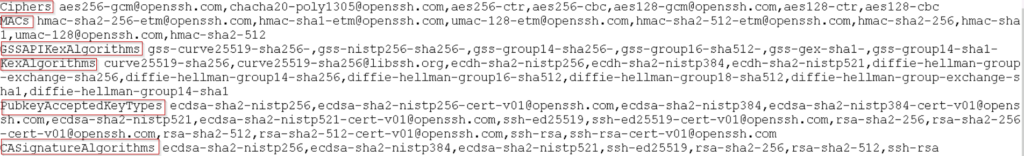
Here you can find existing(active state) Ciphers, Message Authentication Code (MAC) algorithm, GSSAPIKexAlgorithms, KexAlgorithms ,PubkeyAcceptedKeyTypes, CASignatureAlgorithms.
step3: Copy the KexAlgorithms content into a notepad as described above screenshot and remove those 3 sha1 based key exchange algorithms.
After removing those 3 sha1 based keys from notepad, you will get below content.
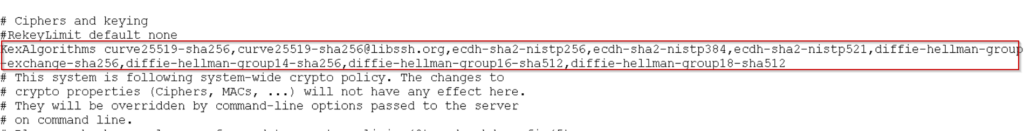
KexAlgorithms curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-grou p-exchange-sha256,diffie-hellman-group14-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512
Now Copy the content from notepad and past it into /etc/ssh/sshd_config file as shown below.
Save and exit from sshd_config file.
Step4: Before restarting SSH, verify the configuration file by using below command.
sshd -t
Step5: You can restart the SSHD service if there are no errors reported.
systemctl restart sshd
Step6: The diffie-hellman-group-exchange-sha1 should no longer be listed in the debug kex names logs after establishing the SSH connection with verbose mode.
ssh -vvv username@IP-Address
Conclusion:
Disable diffie-hellman-group1-sha1 for SSH issue has been fixed successfully. If you have any questions about this topic, please leave a comment. In my previous article discussed about Deprecated SSH Cryptographic Settings from Qualys scan