The purpose of this article is to provide a brief introduction to VMware NSX data center.
The VMware NSX network virtualization platform provides data center operators with the operational model of a VM for their data center networks. As they implement software-defined data centers, they can gain greater agility, efficiency and provisioning speed while reducing complexity. Network security is an often-overlooked feature set, fundamental to VMware NSX.
VMware NSX Data Center
Generally, for virtualizing a single physical machine, VMware vSphere makes use of x86 servers and software. The NSX virtualization platform leverages encapsulation to virtualize Layer 2 switching and Layer 3 routing from existing networks. Would like to check more about NSX product.
NSX is the Software-Defined Networking (SDN) solution for Software-Defined Data Center (SDDC) from VMware. Two types of NSX.
- NSX-V it is designed and focused on VMware vSphere and Virtual Machine (VM).
- NSX-T it is decoupled from VMware vSphere, VMware vCenter Server, VMware ESXi .it can work other hypervisor KVM (for Kernel-based Virtual Machine) and containers like (Docker and Kubernetes).
Software-Defined Data Center (SDDC) has three major building blocks called as network, storage and server virtualization.
Isolation is one of the main characteristics of network virtualization.
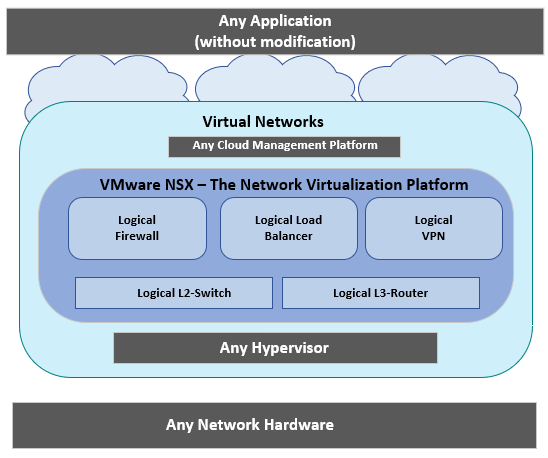
NSX is a platform bring solutions to Network and Security. It reproduces the entire network model into a software by enabling any Network Topology, and also enables library of logical network elements and services.
NSX will give you all the networking and security services into software without any dependence on underlying hardware. NSX provides switching, Routing, load balancing, connectivity to physical networks, firewalling, VPN, data security, activity monitoring.
→ You can take any Network Hardware, there will be no dependence on router or switch or firewall from any vendors. The NSX will support any network hardware.
→ Any hypervisor can be installed on any network hardware, and the network virtualization platform will provide a Firewall, Load Balancer, Virtual private network, Network switch, Routers capabilities into the software.
→ You can see Any Cloud Management Platform you can use any existing VMware product solution for orchestration vRealize Automation product integrate and then automate the entire networking deployment for your virtual machines.
Overview Architecture
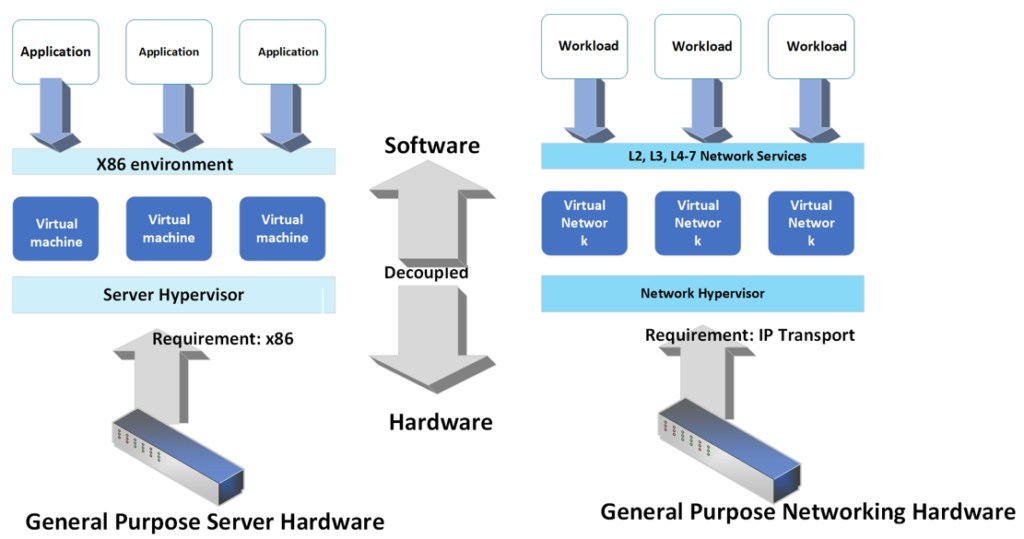
NSX actually provides the same operational model we have seen in traditional hardware. However Here ESXI hypervisor abstracts the physical hardware and decouple the physical hardware and it provides compute CPU and MEMORY capabilities into the software by virtualizing all the hardware for virtual machines.
NSX also does the networking hardware on any switch router etc from any vendor because this hardware is working as a transport layer. It has transport capacity for packet switching and forwarding. Once you install a network hypervisor layer, creating a virtual network, deleting virtual networks on demand without having any dependency for reconfiguration on the physical network. Hence virtual machine migration becomes much easier. You can move your workload anywhere since there is no hardware dependency because the NSX abstraction layer decouples hardware complexity from software layer.
VMware NSX provides a distributed service model like distributed switching, distributed routing, distributed firewall and because of this distributed service model gives you very throughput and east west capability of traffic management.
- The majority of network security is based on isolation, whether for compliance, containment, or just preventing interaction between development, test, and production environments. Isolation and multi-tenancy are intrinsic to network virtualization, whereas manually set and maintained routing, ACLs, and/or firewall rules on physical devices have traditionally been employed to build and enforce isolation.
- By default, virtual networks are cut off from one another and the underlying physical network, maintaining the security principle of least privilege.
- To provide this isolation, no physical subnets, VLANs, ACLs, or firewall rules are necessary. This needs to be said again. NO setup is necessary.
-
Virtual networks are built separately and stay separately unless they are deliberately joined.
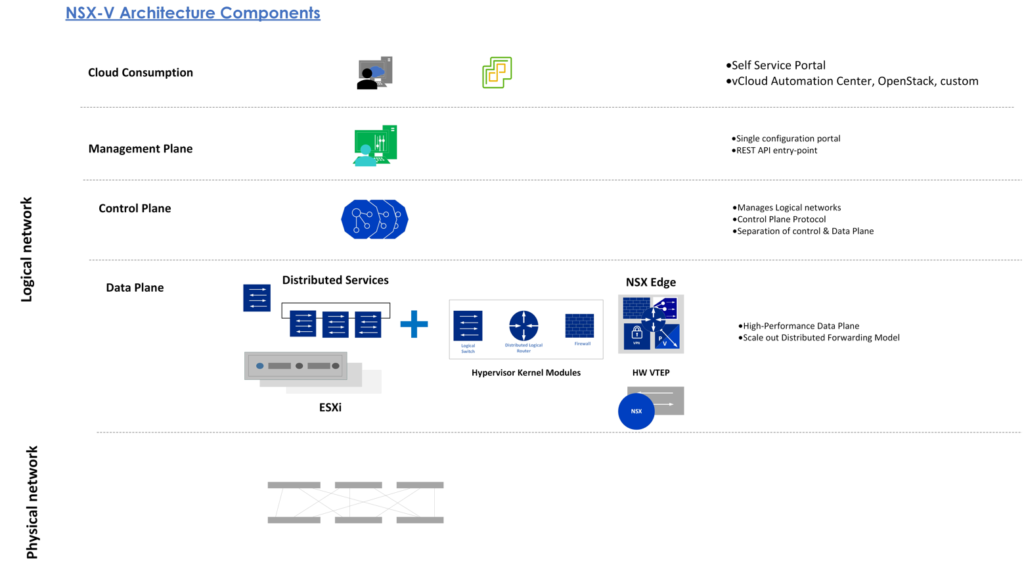
Components
- Physical Network: we need it for transport capacity for packet forwarding and switching, routing as well.
- Data plane: It is responsible for VLAN Switching and Routing firewall.
- Control Plane: it is responsible for control plane operations and NSX controller for control plan function. it is considered the heart of NSX architecture because the NSX controller actually manages logical switching and routing. The NSX Controller cluster is a scale-out distributed system, it contains three NSX Controller nodes.
- NSX controllers maintain NSX network topology information and transfer it to the data plane components.
- Management plane: The NSX manager sits on the management plane and responsible for all management operations. It is a single Virtual machine.
- Cloud Consumption: It is a layer is just about a self-service portal.
- Network segmentation: It is a fundamental feature of VMware NSX network virtualization, just like isolation. A multi-tier network environment, or numerous L2 segments with L3 segmentation or micro-segmentation on a single L2 segment utilizing distributed firewall rules, can be supported by a virtual network.
Conclusion:
In both private and public cloud environments, NSX makes operationalizing Zero Trust security for apps feasible and effective. NSX enables micro-segmentation to design and enforce network security policy at the individual workload level, whether the objective is to shut down essential applications, create a logical demilitarized zone (DMZ) in software, or decrease the attack surface of a virtual desktop environment.
Thanks for your time, leave a comment if you have any queries about VMware NSX data center.