In this article discuss about Disable TLS 1.0 and TLS 1.1 on Windows Server machines. Transport Layer Security protocol (TLS) 1.1 to be decommissioned this spring in support of an updated security protocol The NIH Information Security Program has directed eRA to decommission TLS 1.1 as a result of an updated cryptographic protocol being implemented.
The purpose of this post is to provide you with information about how to ensure the security of your infrastructure by enabling TLS 1.2 on your Windows Server.
Using TLS 1.2 or TLS 1.3, attackers will have difficulty eavesdropping on communications because of their resistance to man-in-the-middle attacks.
Transport Layer Security 1.3 simplifies the handshake process and removes unnecessary cryptographic overhead, which results in a faster connection time.
THREAT:
TLS can generate public and private key pairs using a variety of cyphers (algorithms). For instance, if TLSv1.0 employs the RC4 stream cypher or a block cypher in CBC mode. The biases in RC4 are well known, and the block cypher in CBC mode is vulnerable to the POODLE attack. TLSv1.0 includes a mechanism for a TLS implementation to downgrade the connection to SSL v3.0, thereby weakening security, if configured to use the same cypher suites as SSLv3.
IMPACT:
An attacker can use cryptographic flaws to launch man-in-the-middle attacks or decrypt communications. An attacker could, for example, force a downgrade from TLS to the older SSLv3.The POODLE vulnerability can be exploited to read secure communications or modify them maliciously if the protocol is Zero.
SOLUTION:
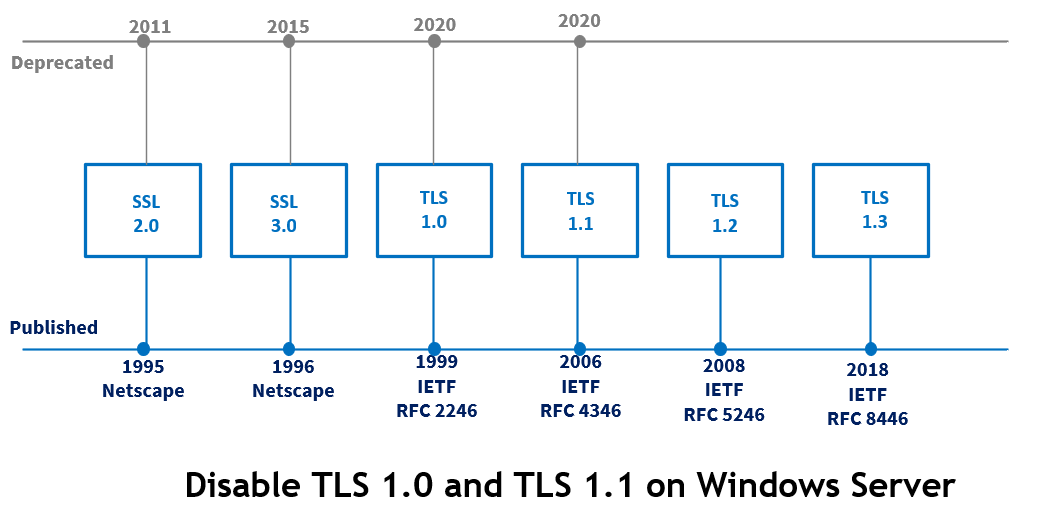
Due to several attacks found in recent years that put encrypted internet communications relying on the two protocols at risk, the Internet Engineering Task Force (IETF) has formally deprecated the TLS 1.0 and TLS 1.1 cryptographic protocols.
The IETF now recommends that all businesses, government agencies, and software developers use the two most recent versions of the TLS standard, TLS 1.2 and TLS 1.3, both of which are deemed secure connection.
Check TLS 1.0 and TLS 1.1 status on Windows
TLS 1.1 is used to encrypt traffic on the web server, but this protocol was deprecated by the US government in March 2021 due to concerns over security.
By using below syntax, we can check ssl/tls status. In order to execute we need to install openssl package in windows machine.
openssl s_client -connect ip:port -tls1
Step1:
Create a key on Windows Registry using PowerShell Command as mentioned below
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Force
Output:
Hive: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2 Name Property ---- -------- Server
As per above output we could see in Property TLS1.2 is not existing.
Procedure to enable TLS
As a part of prerequisite first Disable SSL 2.0, SSL 3.0, TLS 1.0, TLS 1.1 in Windows Registry
After disabling SSL2.0, SSL3.0, TLS1.0 and TLS1.1 reboot the machine. Now create a DWORD value as per below PowerShell command
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' –PropertyType 'DWORD' -Name 'DisabledByDefault' -Value '0'
Output:
PS C:\Users\Administrator> New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -PropertyType 'DWORD' -Name 'DisabledByDefault' -Value '0' DisabledByDefault : 0 PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2 PSChildName : Server PSDrive : HKLM PSProvider : Microsoft.PowerShell.Core\Registry
Step2:
Enable the TLS1.2 as per below PowerShell command
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' –PropertyType 'DWORD' -Name 'Enabled' -Value '1'
Output:
PS C:\Users\Administrator> New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -PropertyType 'DWORD' -Name 'Enabled' -Value '1'
Enabled : 1 PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2 PSChildName : Server PSDrive : HKLM PSProvider : Microsoft.PowerShell.Core\Registry
Step3:
Create a key for TLS1.2 client version as per below PowerShell command
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force
Output
PS C:\Users\Administrator> New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force Hive: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2 Name Property ---- - ------- Client
Enable the TLS1.2 by adding DWORD (32-bit) value as shown below
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' –PropertyType 'DWORD' -Name 'DisabledByDefault' -Value '0
Output
PS C:\Users\Administrator> New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -PropertyType 'DWORD' -Name 'DisabledByDefault' -Value '0' DisabledByDefault : 0 PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2 PSChildName : Client PSDrive : HKLM PSProvider : Microsoft.PowerShell.Core\Registry
Step4:
TLS 1.2 can be enabled by using the registry keys and values listed below
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -PropertyType 'DWORD' -Name 'Enabled' -Value '1'
Output:
PS C:\Users\Administrator> New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -PropertyType 'DWORD' -Name 'Enabled' -Value '1' Enabled : 1 PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2 PSChildName : Client PSDrive : HKLM PSProvider : Microsoft.PowerShell.Core\Registry
You can double check the setting in Windows Registry by using below path you could find disable TLS 1.0 and TLS 1.1 settings
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\
Conclusion:
Successfully enabled Transport Layer Security (TLS) 1.2 and disable TLS 1.0 and TLS 1.1 in windows server operating system. This procedure is similar to all kind of windows server operating system.
Thanks for reading this article. I hope you find it useful. If you have a question about the disable TLS 1.0 and TLS 1.1 topic let me know.