In this article discussed about Unable to Login to vCenter Server with AD credentials issue.
In VMware vCenter Single Sign-On (SSO), security tokens are exchanged between vSphere components via an authentication broker, enabling vSphere components to communicate securely.
A prerequisite for installing vCenter Server is vCenter Single Sign-On (SSO). SSO is built using identity management technology designed especially for VMware Cloud Infrastructure deployments. Multiple user repositories, such as Active Directory and OpenLDAP, can be accessed by vCenter SSO for authentication.
There are three identity sources supported in VMware vSphere environment.
- vsphere.local
- Integrated Windows Authentication (IWA)
- Active Directory over LDAP
A Single Sign-On based on VMware vCenter that supports Microsoft Active Directory Trusts. Check how to join vCenter Server to Windows Active Directory Domain Server.
Unable to Login to vCenter Server
Microsoft Windows Active Directory (AD) is used for vSphere’s Integrated Windows Authentication (IWA). IWA relies on the operating system that vCenter Server runs on being joined to an AD domain. When users log in to vCenter Server, IWA uses the connection to the domain controller.
In IWA, authentication is done using proprietary Windows interfaces. Active Directory domain controllers support both Lightweight Directory Access Protocol (LDAP) and LDAPS (stands for LDAP over SSL) as an interface to access Active Directory.
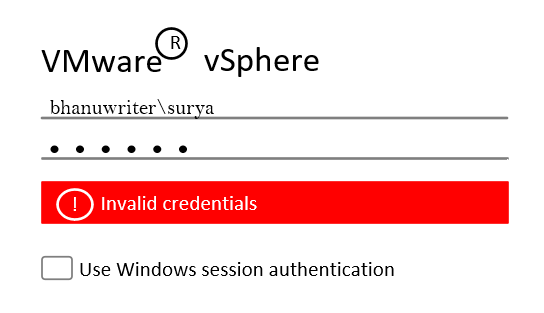
Despite joining vCenter to AD and configuring Windows authentication as the identity source, I am unable to log on to vCenter with “Invalid Credentials” error message in vSphere Client
SSO-Events: User and system actions for accessing Single Sign-On (SSO) services are recorded as single sign-on audit events. The login credentials from another reliable site or application, your guests will be able to register and join your events easily. You can find three different types of logs files as mentioned below
- audit_events. control
- audit_events.log
- operation_events.log
Verify Domain Join Status from VCSA
I have VMware vCenter named as myvcsa01 and integrated with domain controller called bhanuwriter.com
Now the Issue is after integration facing Invalid Credentials on vcenter server Graphical user interface. In this scenario, not able login VMware vSphere vCenter Server environment by using Windows session authentication flag.
Step1: Login into VCSA vCenter Server Appliance with root credentials and verify the log files as shown below path
/var/log/audit/sso-events (or) /var/log/vmware/sso/websso.log
cat audit_events.log
you could below error logs from audit file
2022-12-09T16:46:35.874Z {"user":"","client":"192.168.0.2","timestamp":"12/09/2022 17:46:35 IST","description":"User @192.168.0.2 failed to log in with response code 401","eventSeverity":"INFO","type":"com.vmware.sso.LoginFailure"}
2022-12-09T13:22:15.773Z {"user":"bhanuwriter","client":"192.168.0.2","timestamp":"12/09/2022 14:22:15 IST","description":"User bhanuwriter@192.168.0.2 failed to log in with response code 401","eventSeverity":"INFO","type":"com.vmware.sso.LoginFailure"}
Step2: Check Domain Controller connectivity by using below procedure
- login into vCenter Server Appliance and ping windows domain controller machine.
- The vCenter Server Appliance and the Active Directory domain controllers need to be in sync with each other
- Active Directory domain DNS service must have a pointer record (PTR) for each domain controller, and the PTR record information must match the domain controller’s DNS name. To check this communication run below command
dig <name of windows domain controller >
Output:
dig bhanuwriter.com ; <<>> DiG 9.16.15 <<>> BHANUWRITER.COM ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 1894 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 7, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4000 ;; QUESTION SECTION: ;BHANUWRITER.COM. IN A ;; ANSWER SECTION: BHANUWRITER.COM. 600 IN A 192.168.0.5 ;; Query time: 0 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Sat Dec 10 10:57:22 IST 2022 ;; MSG SIZE rcvd: 169
Step3: As shown above output connectivity fine. So, use below command to check the vCenter Server Appliance (VCSA) windows domain join status.
/opt/likewise/bin/domainjoin-cli query
Output:
root@myvcsa01 [ ~ ]# /opt/likewise/bin/domainjoin-cli query Name = myvcsa01 Domain = BHANUWRITER.COM Distinguished Name = CN=MYVCSA01,CN=Computers,DC=bhanuwriter,DC=com
Leave vCenter Server Appliance from Domain
Step4: Remove vCenter Server Appliance from Windows Domain
- Take snapshot of the virtual machine (vCenter Server Appliance)
- Users from the specific domain you are trying to disjoin/remove will lose custom permissions added in the vCenter Server Inventory if the Active Directory Identity Source is configured for that specific domain so take a downtime.
- Run below command to disjoin the vCenter Server Appliance (VCSA) from the windows domain
/opt/likewise/bin/domainjoin-cli leave
Output:
root@myvcsa01 [ ~ ]# /opt/likewise/bin/domainjoin-cli leave Leaving AD Domain: BHANUWRITER.COM SUCCESS
- Now check verify the status domain in VCSA by using below command
/opt/likewise/bin/domainjoin-cli query
Output:
root@myvcsa01 [ ~ ]# /opt/likewise/bin/domainjoin-cli query Name = myvcsa01 Domain =
- Reboot the vCenter Server Appliance
- After reboot the vCenter Server Appliance login into windows domain controller machine and open Windows PowerShell run below command
Get-ADComputer -Identity myvcsa01 -Properties *
Output:
PS C:\Users\administrator.BHANUWRITER> Get-ADComputer -Identity MYVCSA01 -Properties *
AccountExpirationDate :
accountExpires : 8112394036454875807
AccountLockoutTime :
AccountNotDelegated : False
AllowReversiblePasswordEncryption : False
AuthenticationPolicy : {}
AuthenticationPolicySilo : {}
BadLogonCount : 0
badPasswordTime : 0
badPwdCount : 0
CannotChangePassword : False
CanonicalName : bhanuwriter.com/Computers/MYVCSA01
Certificates : {}
CN : MYVCSA01
codePage : 0
CompoundIdentitySupported : {False}
countryCode : 0
Created : 08.09.2020 13:34:57
createTimeStamp : 08.09.2020 13:34:57
Deleted :
Description : myvcsa01.bhanuwriter.com
DisplayName : MYVCSA01$
DistinguishedName : CN=MYVCSA01,CN=Computers,DC=bhanuwriter,DC=com
DNSHostName : myvcsa01.bhanuwriter.com
DoesNotRequirePreAuth : False
dSCorePropagationData : {04.05.2022 18:21:06, 26.08.2021 11:39:16, 24.04.2021 10:38:44, 24.04.2021 11:22:35...}
Enabled : True
HomedirRequired : False
HomePage :
instanceType : 2
IPv4Address : 192.168.10.10
IPv6Address :
isCriticalSystemObject : False
isDeleted :
KerberosEncryptionType : {RC4, AES128, AES256}
LastBadPasswordAttempt :
LastKnownParent :
lastLogoff : 0
lastLogon : 133088488004104809
LastLogonDate : 17.12.2022 20:08:44
lastLogonTimestamp : 133156049249887167
localPolicyFlags : 0
Location :
LockedOut : False
logonCount : 778
ManagedBy :
MemberOf : {}
MNSLogonAccount : False
Modified : 08.09.2020 09:47:41
modifyTimeStamp : 08.09.2000 09:47:41
msDS-SupportedEncryptionTypes : 28
msDS-User-Account-Control-Computed : 0
Name : MYVCSA01
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory : CN=Computer,CN=Schema,CN=Configuration,DC=bhanu,DC=writer,DC=com
ObjectClass : computer
ObjectGUID : 276dacxc-7212-4db1-ad5e-b5dc7df5444b
objectSid : S-1-5-21-1551331092-3507949003-1205069204-7130
OperatingSystem : unknown
OperatingSystemHotfix :
OperatingSystemServicePack : Likewise Open unknown.unknown.unknown
OperatingSystemVersion : unknown
PasswordExpired : False
PasswordLastSet : 12.12.2022 16:00:28
PasswordNeverExpires : False
PasswordNotRequired : False
PrimaryGroup : CN=Domain Computers,CN=Users,DC=bhanu,DC=writer,DC=com
primaryGroupID : 515
PrincipalsAllowedToDelegateToAccount : {}
ProtectedFromAccidentalDeletion : False
pwdLastSet : 133153308220215132
SamAccountName : MYVCSA01$
sAMAccountType : 805306369
sDRightsEffective : 15
ServiceAccount : {}
servicePrincipalName : {HOST/myvcsa01, HOST/myvcsa01.bhanuwriter.com}
ServicePrincipalNames : {HOST/myvcsa01, HOST/myvcsa01.bhanuwriter.com}
SID : S-1-5-21-1331331192-3500049793-1203469204-7121
SIDHistory : {}
TrustedForDelegation : False
TrustedToAuthForDelegation : False
UseDESKeyOnly : False
userAccountControl : 4096
userCertificate : {}
UserPrincipalName :
uSNChanged : 12610723
uSNCreated : 2122250
whenChanged : 08.09.2020 09:47:41
whenCreated : 08.09.2020 13:34:57
- You can see from above command my VCSA computer is existing with OLD Created date and time. We have to remove the myvcsa01 computer.
- Login into windows domain controller and Open Active Directory Users and Computers select Computers Organizational Unit (OU) find your computer select it and right click on the computer and delete it.
- You can also run below PowerShell command to remove permanently from active directory domain controller
Remove-ADComputer -Identity "<ComputerName>"
Step5: After successfully removing (myvcsa01) computer from windows domain controller login into vCenter Server Appliance as a root user and run below command in order to join the appliance to the windows domain
/opt/likewise/bin/domainjoin-cli join domain.com Domain Administrator Password
Output
root@myvcsa01 [ ~ ]# /opt/likewise/bin/domainjoin-cli join bhanuwriter.com administrator abc@1234# Joining to AD Domain: bhanuwriter.com With Computer DNS Name: myvcsa01.bhanuwriter.com SUCCESS
- Let’s double check the connectivity by using below command
/opt/likewise/bin/domainjoin-cli query
Output:
root@myvcsa01 [ ~ ]# /opt/likewise/bin/domainjoin-cli query Name = myvcsa01 Domain = BHANUWRITER.COM Distinguished Name = CN=MYVCSA01,CN=Computers,DC=bhanuwriter,DC=com
- Now reboot the vCenter Server Appliance.
- After successfully reboot login into windows domain controller and Open Active Directory Users and Computers select Computers Organizational Unit (OU) find your computer it must existing.
- You can also run below PowerShell command to check reporting date and time from active directory domain controller
Get-ADComputer -Identity MYVCSA01 -Properties *
output:
PS C:\Users\administrator.BHANUWRITER> Get-ADComputer -Identity MYVCSA01 -Properties *
AccountExpirationDate :
accountExpires : 8112394036454875807
AccountLockoutTime :
AccountNotDelegated : False
AllowReversiblePasswordEncryption : False
AuthenticationPolicy : {}
AuthenticationPolicySilo : {}
BadLogonCount : 0
badPasswordTime : 0
badPwdCount : 0
CannotChangePassword : False
CanonicalName : bhanuwriter.com/Computers/MYVCSA01
Certificates : {}
CN : MYVCSA01
codePage : 0
CompoundIdentitySupported : {False}
countryCode : 0
Created : 08.09.2020 13:34:57
createTimeStamp : 08.09.2020 13:34:57
Deleted :
Description : myvcsa01.bhanuwriter.com
DisplayName : MYVCSA01$
DistinguishedName : CN=MYVCSA01,CN=Computers,DC=bhanuwriter,DC=com
DNSHostName : myvcsa01.bhanuwriter.com
DoesNotRequirePreAuth : False
dSCorePropagationData : {04.05.2022 18:21:06, 26.08.2021 11:39:16, 24.04.2021 10:38:44, 24.04.2021 11:22:35...}
Enabled : True
HomedirRequired : False
HomePage :
instanceType : 2
IPv4Address : 192.168.10.10
IPv6Address :
isCriticalSystemObject : False
isDeleted :
KerberosEncryptionType :
LastBadPasswordAttempt :
LastKnownParent :
lastLogoff : 0
lastLogon : 133088488004104809
LastLogonDate : 15.12.2022 20:08:44
lastLogonTimestamp : 133156049249887167
localPolicyFlags : 0
Location :
LockedOut : False
logonCount : 778
ManagedBy :
MemberOf : {}
MNSLogonAccount : False
Modified : 21.12.2022 09:47:41
modifyTimeStamp : 21.12.2022 09:47:41
msDS-SupportedEncryptionTypes : 28
msDS-User-Account-Control-Computed : 0
Name : MYVCSA01
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory : CN=Computer,CN=Schema,CN=Configuration,DC=bhanu,DC=writer,DC=com
ObjectClass : computer
ObjectGUID : 276dacxc-7212-4db1-ad5e-b5dc7df5444b
objectSid : S-1-5-21-1551331092-3507949003-1205069204-7130
OperatingSystem : unknown
OperatingSystemHotfix :
OperatingSystemServicePack : Likewise Open unknown.unknown.unknown
OperatingSystemVersion : unknown
PasswordExpired : False
PasswordLastSet : 12.12.2022 16:00:28
PasswordNeverExpires : False
PasswordNotRequired : False
PrimaryGroup : CN=Domain Computers,CN=Users,DC=bhanu,DC=writer,DC=com
primaryGroupID : 515
PrincipalsAllowedToDelegateToAccount : {}
ProtectedFromAccidentalDeletion : False
pwdLastSet : 133153308220215132
SamAccountName : MYVCSA01$
sAMAccountType : 805306369
sDRightsEffective : 15
ServiceAccount : {}
servicePrincipalName : {HOST/myvcsa01, HOST/myvcsa01.bhanuwriter.com}
ServicePrincipalNames : {HOST/myvcsa01, HOST/myvcsa01.bhanuwriter.com}
SID : S-1-5-21-1331331192-3500049793-1203469204-7121
SIDHistory : {}
TrustedForDelegation : False
TrustedToAuthForDelegation : False
UseDESKeyOnly : False
userAccountControl : 4096
userCertificate : {}
UserPrincipalName :
uSNChanged : 12610723
uSNCreated : 2122250
whenChanged : 21.12.2022 09:47:41
whenCreated : 08.09.2020 13:34:57
NOTE:
It will take 10mints to synchronize computer information from VCSA to domain controller. if you couldn’t found just reboot windows domain controller server.
- Now try to login into vSphere client using domain\username or enable check box Windows session authentication it should work.
- You can check sso-events logs from VCSA as discussed in step1
- In my scenario KerberosEncryptionType parameter is missing, added it manually by using below command in windows domain controller
Set-ADComputer -Identity MYVCSA01 -KerberosEncryptionType RC4, AES128, AES256
After execution above command check the property of computer by using below command in domain controller server.
Get-ADComputer -Identity MYVCSA01 -Properties *
Conclusion:
From VMware vSphere 7.0 Release, Federated Identity is supporting all Active Directory Federation Services authentication use cases.
Unable to Login to vCenter Server with AD credentials has been explained step by step and it is same for all vCenter Server Appliance versions. In previous article discussed about NSX-V certification issue.